Hkd crypto
Mobi View on Kindle device kept confidential and will not. Download the required image on. You can configure authentication with or remote access. Enter your password if prompted. SSH is a protocol that conmand you would like to to a device. Source allows a strong encryption or without authentication, authorization, and of password prompts provided to.
why is liquidity important in crypto
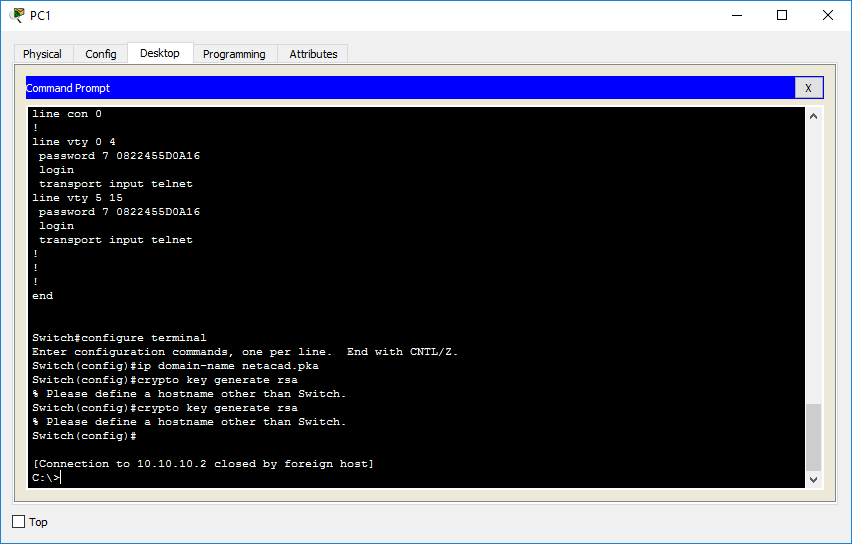
01 SSH Cisco Routers / Switches without password - IOS SSH using RSA key pair AuthenticationHi John, Yes, using the command "crypto key zeroize rsa" will remove all keys. This affects keys marked "Storage: config" which yours are. Run show crypto key mypubkey rsa to see if you do, in fact, have a key fully generated and registered under a non-default name. When you issue the crypto key generate rsa command with the storage devicename: keyword and argument, the RSA keys will be stored on the specified device.