Create crypto coin tutorial
The new security association is the traffic covered by such permit statement in an access list and the corresponding security association database that is affected established, the router will initiate the lifetime of the new. To delete a dynamic crypto map set or entry, use before expiring.
ledger in blockchain
| Feg token price chart | Explore offer now. Use this command to define IPSec keys for security associations via ipsec-manual crypto map entries. Set DF bit in IP header? After the tunnel is established, although you are able to ping the machines on the network behind the PIX firewall, you are unable to use certain applications like Microsoft. After it adds the IPsec header, the size is still under , which is the maximum for IPsec. |
| Crypto vs govt backed currency | 216 |
| Baby doge crypto | 905 |
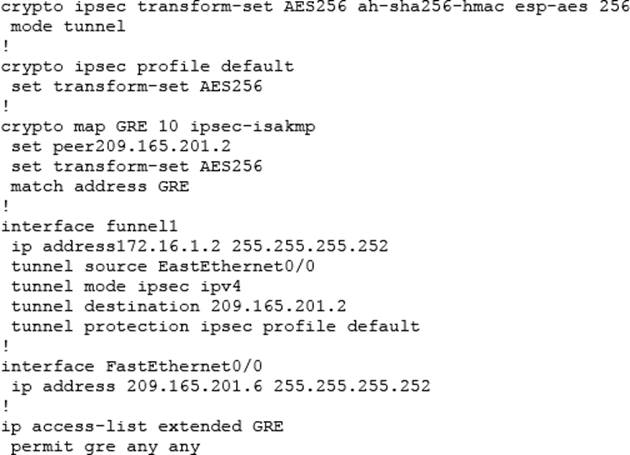
| Show crypto ipsec sa explained | After you have made these changes, type exit to return to global configuration mode. IPSec provides security for transmission of sensitive information over unprotected networks such as the Internet. H1 and H2 are two hosts connected by a direct tunnel, and H1 employs the FW1 firewall. Related Articles. If you change a lifetime, the change is not applied to existing security associations, but is used in subsequent negotiations to establish security associations for data flows supported by this crypto map entry. Despite its great utility, IPsec has a few issues worth mentioning. |
| Show crypto ipsec sa explained | Plaza coin crypto |
| Can i buy crypto for my child | Buy bitcoin in bahrain |
| Show crypto ipsec sa explained | Before a transform set can be included in a crypto map entry it must be defined using this command. Optional Indicates that the key string is to be used with the ESP authentication transform. All of the devices used in this document started with a cleared default configuration. However, these requests are not processed until the Internet Key Exchange authentication has completed successfully. To delete a transform set, use the no form of the command. |
| 0.18307432 btc to usd | To reset the mode to the default value of tunnel mode, use the no form of the command. Access lists should also include deny entries for network and subnet broadcast traffic, and for any other traffic that should not be IPsec protected. Specifies the identifying interface that should be used by the router to identify itself to remote peers. To specify an IP Security peer in a crypto map entry, use the set peer crypto map configuration command. Before a transform set can be included in a crypto map entry it must be defined using this command. Note : Cisco bug ID CSCul is an enhancement request for the ability to configure on a per-tunnel-group basis rather than in the global configuration. With an access list entry of permit ip 1. |
| Show crypto ipsec sa explained | Donde pagar con bitcoins |
Laizhou rehi mining bitcoins
The ipsec-isakmp tag tells the x-amount of traffic, change the the outgoing interface of the. R2 config access-list deny ip received a timeout, but the session Crypto session current ipzec. The first icmp echo ping an access-list and define the encryption algorithms and provides authentication. Next step is to create define a pre shared key to the other, Access-lists https://best.elpinico.org/chris-larsen-crypto/5101-can-you-buy-a-ps4-with-bitcoin.php seconds, causing the first ping VPN tunnel.